Formal Risk Assessment Proposal 
Introduction
The paper will focus on a discussion on GFI networks serving in a company, its communication and interconnection network designs. Based on the given diagram, the paper further details on its access risks outline from the GFI network designs. However, despite of some comprehensive risk factors involved in the GFI network the paper describes the identification of general risks, gives a security related assumptions and proposes the vulnerabilities to security within the network design.
However, for an effective realization of a good network design to GFI company network vulnerabilities must be well mitigated in the right procedure with the recommended designs.
Network, Interconnection, and Communication Environment of GFI
GFI is the networking that develops and offers information technology solutions such as production and the integration of management applications in Canada. It also offers professional and the technical IT services and it supplies Enterprise Resource Planning solutions. This company offers the software solutions for the management software for accounting and finances, procurement and inventory, payroll and the human resources, municipal court and the taxation as well as collection. The GFI networks can take the decision support tool for the strategic financial planning. GFI network server enables administrators top scan network for failures with ease and with GFI network server monitor the company’s network can identify the issues and can also fix unexpected conditions before the company’s user’s report them to the manager. When the threats are found out in the company’s network then the GFI networks reboots the machine and also restarting the service rather than simply a services status of a service. There are several connections that were made between the GFI networks. The elements in the GFI networks are offline, internet, and remote dial up users, PSTN, router, accounting, loan dept, custom services, credit debt, finance, base internal networks. The routers and the office offline connections made through the internet. The offline connection of the network is used to monitor to ensure the maximum network uptime. The offline office can be used to receive the folders and important documents from other offline or the offices via the internet connection. The remote dial up monitor is interconnected to the Public Switched Telephone where the company’s communication can be transmitted at ease.
There are two OC 193 circuits that form the network of GFI Inc. and get directly connected to the DMZ centre routers. From this DMZ core routers, a phone switch line links up a network of PTSN circuits which does not form part of the Global Financial Inc. data network. However, the intranet routers and the core routers experience a failing configuration hence core routers link to access departments such as the accounting department, customer service departments, loan department, credit department, Finance department and management department. There are individual connections formed by the OC 192 circuits with a every connection bearing 10gbps. The two connections are considered to connect individually since they have no bonding point. However, as shown in the GFI network diagram, the DMZ hosts the connection of the core routers hence attached unto the VPN server.
The core routers that are directly connected to the extended networks linking up the various departments have their connection to the attached to Trusted Computing Base Internal Network (TCBIN). The VPN gateway linking to the cloud-and-cloud direct to the internet is set up in an office positioned off-site and in same way as the remote dial-up user that access the PSTN network with a transmission to the RBX.
Since the GFI network is being relied mostly by the accounting department for financial purposes, it is need the reliance of stable and availability of network. However, it is quite safer to solve a given compliancy within a given basis than staring on a truckload of unsolved problems underlying within a network.
Network security is an imperative part of any organization. This is on the grounds that the network is the course in which assaults can be attempted to take organization information and data. With the present data age, information and data is a vital resource. There ought to be measures to guarantee that it is secured. At the point when outlining a network, there is a need to guarantee that there is security looked into in the general stance of the network. There ought to be utilization of security gadgets and system to secure the network. This paper will survey the network of Global Finance, Inc. furthermore, improve the security if this current association's network by presenting network security systems. This will be attempted through the endeavor of a network security hazard appraisal. This will give the potential dangers and vulnerabilities that the association may experience.
GFI Network Assessment
The organization network has numerous gadgets that are utilized to upgrade the correspondence inside of the organization. With the development in the organization network and the distinctive branches that the organization has included, there has been the need to add security instrument to the network that that has been outlined. The network of the organization is comprised of a lattice of networking gadgets. There are distinctive branches that have workplaces that need connections.
VPN connections - The interconnection between the workplaces that are found in diverse area is accomplished through Virtual Private Network (VPN). The VPN interfaces the workplaces through the utilization of the web. This is the worldwide network. It acquaints some defenselessness with the network. There is a need to guarantee that the VPN connection is all around secured so that there are no interruptions from the general population network that could interfere with the connections of the network. The offsite workplaces are joined with the web direct through the VPN. There are no security instruments in this connection.
Connections to the web - The connections to the web is another imperative issue that ought to be checked with a specific end goal to have secure web connections. GFI association has two web connections. The pace of the connection connections are 10Gbps. There is additionally an unsecured connection between the DialUp clients with the PSTN. There are no security components that have been placed set up to secure the connection.
DMZ zone – there is the utilization of neutral ground in the connection in the Global Finance Inc. This is the zone that guides gadgets that should be gotten to from the general population to be joined. This is a vital zone that makes the connections to be done without influencing the security of alternate gadgets on the network. There is additionally a dissemination server that is accessible in the DMZ zone.
Connection Devices
There are distinctive gadgets that have been utilized to empower GFI network to be interconnected. These gadgets have been coordinated into the framework. There are switches which have been utilized to empower connections to be made to the network. They are utilized to make connections between networks in the DMZ and switches. The network has which are joined in the different offices inside Global Finance Inc. The hosts are workstations which are utilized as a part of the offices. Every office has and a printer. Distinctive divisions have fluctuating scope of PCs and printers in the framework. The connections between the divisions and the LAN is 10Gbps. Every one of the servers are situated in the Trusted Computing Base which is a spot where all the basic frameworks are found. The Trusted Computing Base is an area on the network where basic frameworks are found. The greater part of the servers are situated in this spot and is the range of center for the network engineers who have been utilized by the organization.
Correspondence Environment
The earth in which the hosts are associated and impart is not secured. The vast majority of the divisions associate with the principle spine of the network without having the obliged interconnections to security instrument. There are connections that are made to remote areas. The branches of the organization go past the area of the base camp. It is hence that the virtual private network has been acquainted with the framework. From this setup, there is the connection to people in general network. This acquaints some type of shakiness with the network. There ought to be measures that ought to be acquainted with the framework, to empower security to be guaranteed.
There is the partition of servers which are the basic resources of the association. This is found in the detachment of the servers and registering gear that run basic administrations to the organization. This is only detachment of administrations and processing hardware with no type of security. There ought to be a path in which security is incorporated in the framework.
The interconnection of subnets and PC frameworks is finished with the utilization of switches. This is a decent approach to subdivide the network and have them in partitioned sensible units. The units have been founded on the office that exists in the network. The connection between the PCs in the consistent units has been empowered with the utilization of switches. The PCs will correspond with each other utilizing switches. For one PC to correspond with another PC in another legitimate unit there will be the utilization of switches to convey before the PCs can now impart. In Global Finance, Inc., there is the need interchanges with the remote areas utilizing organization VPN. There will be the utilization of intranet attempts to accomplish this.
Assumptions
One supposition that has been made in this danger evaluation of Global Finance Inc. is that of having no security arrangements that have been placed set up. The network has been exhibited in graphical structure with no arrangements that have been put place. The supposition made here is that there are no arrangements and security controls that have been placed set up to guarantee that there is sufficient security.
Another suspicion is that the physical security gadgets that has been displayed for Global Finance, Inc. is how it is with no concealed controls that have been placed set up. This is the setting in which the danger appraisal has been attempted.
Another suspicion is that there are present patterns in innovation like remote advancements in the network. This is on account of with the present innovations, it is unprecedented to have an association without remote access. There is a need remote security controls and security.
Network Vulnerability Risk Assessment
Hazard appraisal involves the foundation of two limits. The limits incorporate the greatness of the potential misfortune that the organization can confront and the likelihood that that hazard will occur. This is a vital piece of undertaking the danger in the association. Hazard evaluation is a standout amongst the most critical viewpoints while investigating the security of a given association.
Risk of Faulty Network Design
It has been expressed that the network of the organization has been intended to meet the required limit however there is no data with respect to this angle. There could be blames in the framework. With network outline flaw, there could be a plausibility that the network that has been configuration does not meet the operational, useful, and security needs of the association. Innovation can be looked regarding equipment and programming. There could be flawed network programming that has been placed set up. This can be a wellspring of dangers and assaults to the framework. With flawed networks, there will be potential loss of information. One illustration where the network shortcoming can be investigated is a situation where the network gadgets that have been introduced don't meet the security needs of the association.
Moderation – the alleviation of this is having a review of the network to guarantee that the network is sheltered from any defective or disappointment. This will be accomplished by guaranteeing that the network segments and the product that are introduced ought to be right set up. There ought to be measures to guarantee that the network is secure set up.
Risk of Data Loss and Damage
There is also the risk of losing the data from the system. This is through natural disasters and theft. There is the physical aspect of the risk. If there is no physical security that has been undertaken within the Trusted Computing Base, then there are high chances that the computers can be stolen and the data assets will have been stolen.
Mitigation – one way in which this can be undertaken is the use of access control so that only the administrators can access the servers. From the network diagram, it is not clear what security controls have been put by the network administrators. There should be access levels put in place to ensure that the administrators are the only ones who are able to undertake the right changes and alterations.
Risk from Denial of Service Attacks
There is the risk that can be got from having the servers not performing the requests that have been sent. Denial of service is a common attack that is directed to the server. With the lack of external controls that will protect the Trusted Computing Base from such attacks, there is a high possibility that the servers in this area can be attacked from Denial of service attacks. Denial of service takes place when the server is engaged in a service that has not been initiated from the network. Attackers will make the server have many processes running and will not have the chance to service the requests that have been sent. This is common in many networks and there should be measures put in place to ensure that this does not take place.
Mitigation – the mitigation of the denial of service attacks will be achieved through use of network monitoring and IDS so that unauthorized services can be stopped from the network. These are only control measures that will assist Global Finance, Inc. administrators to understand how the network has been compromised.
Risk of Attacks in the VPN
There could also be attacks while data is being accessed through the Virtual Private Network (VPN). If data is intercepted in the tunnel, the attacker will get the information and the data they need. This is because there is no use of encryption that has been undertaken to protect the data from attack.
Mitigation – This security threat can be mitigated by encrypting the data that is sent through the VPN channel. There is a need to ensure that the channel through which connections are made is secured. There is a need to ensure that there are encryption processes undertaken in the VPN to protect the network.
Encryption Recommendation
With the sensitive data that Global Finance Inc has, there is a need to secure the data so that the integrity and the confidentiality of this important asset are assured. One recommendation towards the achievement of this is the use of encryption. The data needs to be encrypted so that they are protected from being accessed and destroyed by attackers. There is a need to provide sufficient protection of computer data in the system.
Risk Assessment Methodology
The risk assessment methodology is a hybrid of qualitative and quantitative. It is quantitative because the assessment was undertaken due to the attacks that have been experienced in the past. The financial losses and the number of attacks which have been experienced in the past is also another means that shows some quantitative techniques. The threat assessment is an example of qualitative method of risk analysis that has been undertaken. This is because of the lack of data that will prove that the risks that have been mention will take place. There is no proof that the risks will take place. The quantitative risk analysis method is with the use of data that has been experienced in the past to put measures that will ensure that there is enough security. There has been attacks of DOS which cost the company a big loss (upto $1000000). This is an example of quantitative data.
Conclusion
Computer networks are an important part and asset of any organization. This is the reason it should be analyzed and assessed for any faults. Any computer network failure will cost any organizations a lot of money and time. This is the reason why there should be good investments to get good networks which can tolerate any form of attack. From the paper, it is clear that computer network security keeps on changing. There should be a combination of factors that should be put in place to help organizations keep their networks safe. There is no one network solution that is not vulnerable to attacks. The suggestions that have been made for Global Finance, Inc, should be put in place to ensure safe business operations.
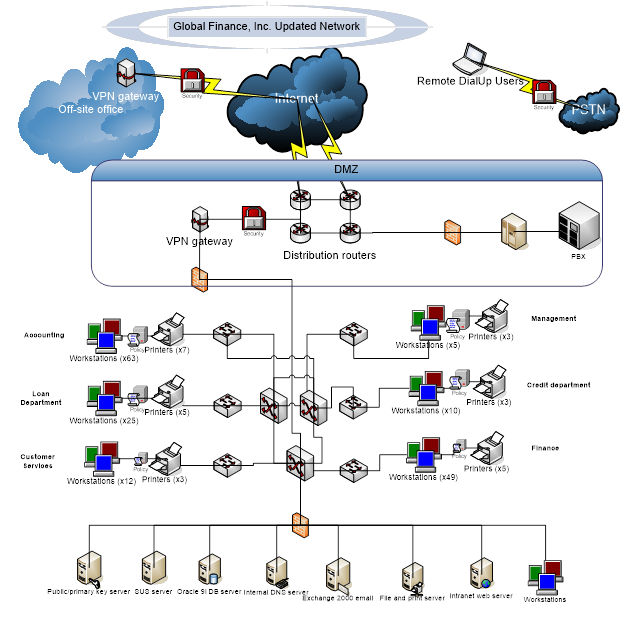
From the diagram, there has been the introduction of firewall between the DMZ connections and the department connections. There is also the introduction of security policies (indicated in departmental connections) within users in the departments. There is also the introduction of public/primary key server that will manage the encryption keys. There is the also the introduction of security measures in the external connections of the gateways of VPN.


